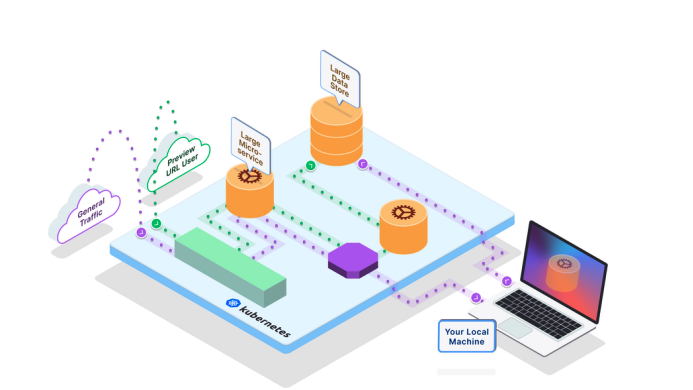
Goal
- Seamless development environment in Kubernetes
- Keep your local development tools, no commit or push required
- Helping local continuous development and deployment of microservice applications
Prerequisites
- telepresence
- kubectl
- k8s cluster
How to
Install Telepresence
Install telepresence on your local laptop, please follow the documentation for the installation steps. The k8s cluster for testing purposes is running on Azure Kubernetes Service. Please set context Kubernetes cluster.
$ kubectlconfig use-context aks-playground-1 $ telepresence connect
When we use the command telepresence connect to the Kubernetes cluster side, Telepresence will create a namespace ambassador and traffic manager deployment. On the client side, Telepresence set up DNS to enable local access to Kubernetes Cluster. So we don’t need kubectl port-forward to manually configure access to local services. When you access a remote service the DNS resolves to a specific IP
address. For more details, see the Telepresence architecture documentation
Telepresence status
Root Daemon: Running Version : v2.4.9 (api 3) DNS : Remote IP : 10.0.0.10 Exclude suffixes: [.arpa .com .io .net .org .ru] Include suffixes: [] Timeout : 4s Also Proxy : (0 subnets) Never Proxy: (1 subnets) User Daemon: Running Version : v2.4.9 (api 3) Ambassador Cloud : Logged out Status : Connected Kubernetes server : https://aks-playground-01-dns-d78da381.hcp. southeastasia.azmk8s.io:443 Kubernetes context: aks-playground-01 Telepresence proxy: ON (networking to the cluster is enabled) Intercepts : 0 total
The Telepresence daemon process creates a Virtual Network Interface (VIF) when Telepresence connects to the Kubernetes cluster
Verify from the client side, the client will get 10.0.0.10 ( kube-dns) as the DNS Server on Virtual Network Interfaces ( tel0 ). The Telepresence
DNS resolver is dynamically configured to resolve names using the namespaces of currently active intercepts.
Link 123 (tel0)
Current Scopes: DNS
LLMNR setting: yes
MulticastDNS setting: no
DNSSEC setting: no
DNSSEC supported: no
DNS Servers: 10.0.0.10
DNS Domain: ~ambassador
~default
~development
~ingress-internal
~kube-node-lease
~kube-public
~kube-system
cluster.local
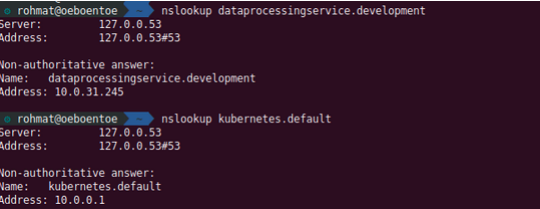
basically, we are able to resolve the service inside kubernetes cluster with the following format servicename.namespaces. for example we try to connect dataprocessingservice on development namespaces
nslookup dataprocessingservice.development
Create a sample deployment in Kubernetes cluster
git clone https://github.com/datawire/edgey-corp-python.git cd edgey-corp-python kubectl apply -f k8s-config/edgey-corp-web-app-no-mapping.yaml -n development
Since this scenario we will access to the ingress, create an ingress object to provide routing rules to verylargejavaservice
spec:
rules:
- host: verylargejavaservice.development.internal
http:
paths:
- backend:
service:
name: verylargejavaservice
Verify the deployment on k8s
kubectl get deployment,svc,ing -n development
NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/dataprocessingservice 1/1 1 1 21m deployment.apps/verylargedatastore 1/1 1 1 21m deployment.apps/verylargejavaservice 1/1 1 1 21m NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/dataprocessingservice ClusterIP 10.0.31.245 <none> 3000/TCP 21m service/verylargedatastore ClusterIP 10.0.4.75 <none> 8080/TCP 21m service/verylargejavaservice ClusterIP 10.0.155.58 <none> 8080/TCP 21m NAME CLASS HOSTS ADDRESS PORTS AGE ingress.networking.k8s.io/verylargejavaservice <none> verylargejavaservice. <none> 21m
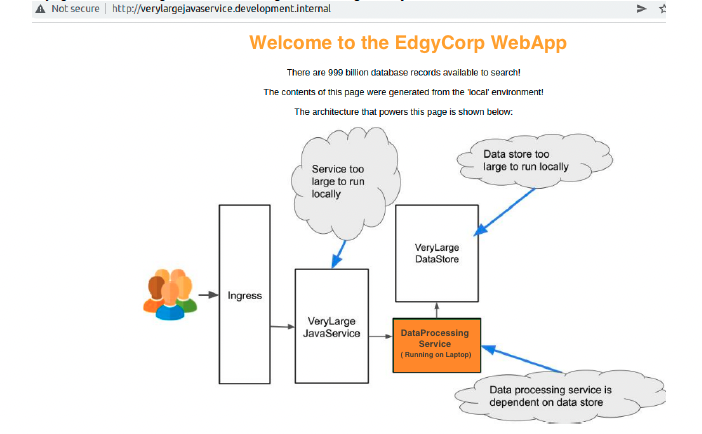
Connection test to verylargejavaservice. below several services, such us verylargejavaservice, dataprocessingservice and verylargedatastore are running on K8s Cluster. Please ignore the wording on the symbol cloud
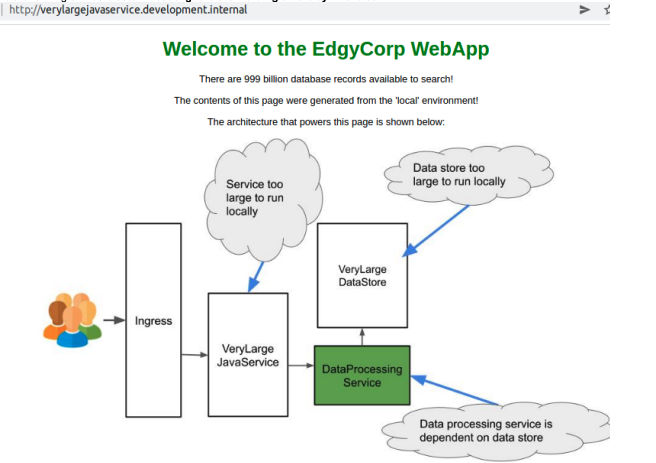
Intercept dataprocessingservice on that running on k8s cluster into your local environment
$ telepresence intercept dataprocessingservice --port 3000 -n development
Using Deployment dataprocessingservice
intercepted
Intercept name : dataprocessingservice-development
State : ACTIVE
Workload kind : Deployment
Destination : 127.0.0.1:3000
Volume Mount Point: /tmp/telfs-2442392270
in parallel you are working on development microservice dataprocessingservice on your laptop, once the intercept is already activated, the traffic from external toward dataprocessingservice will be routed to the local laptop
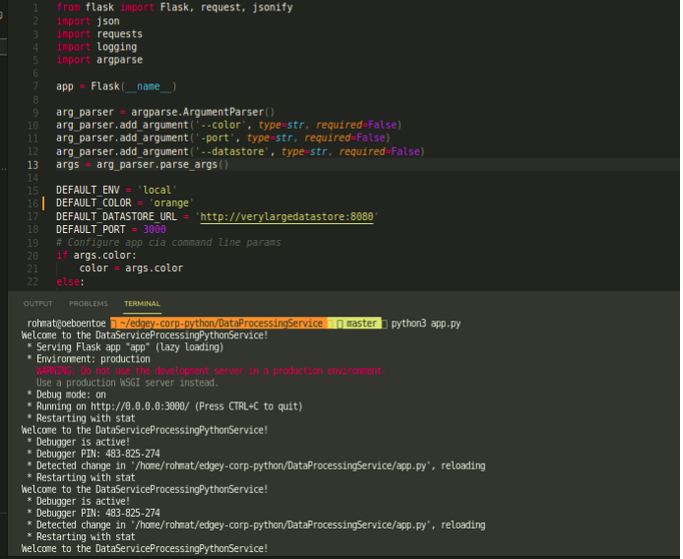
after you make changes code DEFAULT_COLOR = ‘orange’ on local development, we can see the changes when we access the service again, Traffic from verylargejaveservice will be routed to local laptop with orange color.