Integrating OpenVPN with Google Single Sign-On (SSO) streamlines user authentication and access management processes, enhancing security and user experience. By leveraging Google as the identity provider, users can log in to OpenVPN using their Google credentials, eliminating the need for separate usernames and passwords
Prerequisites
- LDAP Gsuite
stunnelopenvpn-auth-ldap
Create LDAP Client
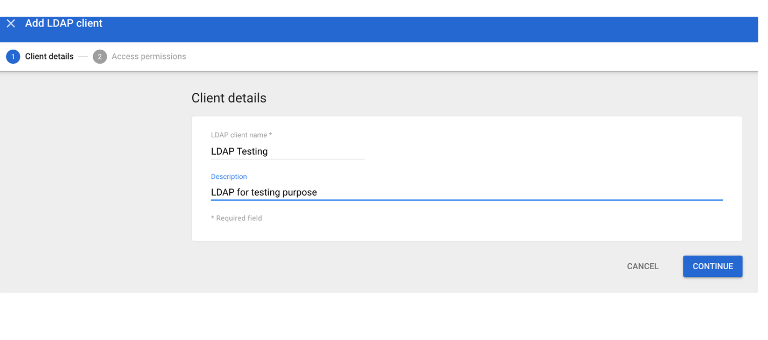
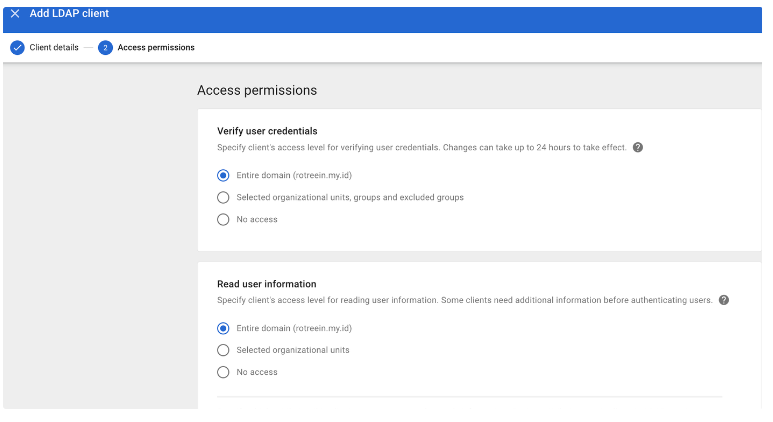
Download the certificate.
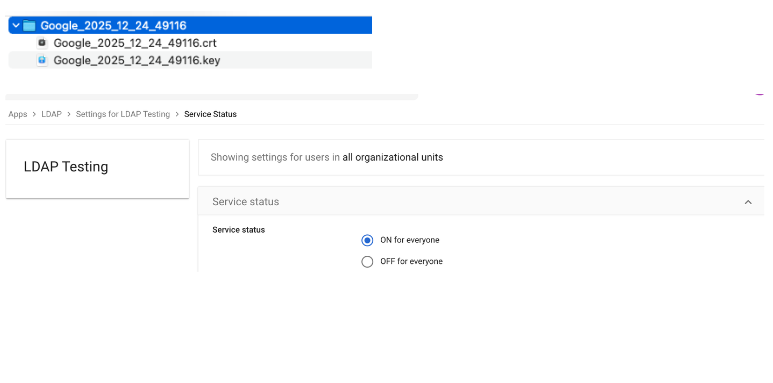
Install package dependencies
Install OpenVPN auth LDAP
apt install openvpn-auth-ldap stunnel4 -yOn this scenario the OpenVPN server is already running, so we just enable integration with google sso
local 172.31.24.60 port 1194 proto udp dev tun ca ca.crt cert server.crt key server.key dh dh.pem auth SHA512 tls-crypt tc.key topology subnet server 10.8.0.0 255.255.255.0 push "route 172.31.0.0 255.255.0.0" push "route 172.35.0.0 255.255.0.0" push "route 172.69.0.0 255.255.0.0" ifconfig-pool-persist ipp.txt log /var/log/openvpn/openvpn.log status /var/log/openvpn/openvpn-status.log keepalive 10 120 cipher AES-256-CBC user nobody group nogroup persist-key persist-tun ##plugin auth-ldap verb 3 crl-verify crl.pem username-as-common-name plugin /usr/lib/openvpn/openvpn-auth-ldap.so /etc/openvpn/auth-ldap.conf verify-client-cert optional #### max-clients 1022 duplicate-cn
Move the LDAP credentials to /etc/openvpn
mv ldap* /etc/openpnCreate config file in /etc/openvpn/auth-ldap.conf
<LDAP> URL ldaps://ldap.google.com:636 # Timeout 15 TLSEnable false TLSCACertDir /etc/ssl/certs TLSCertFile /etc/openvpn/ldap-client.pem TLSKeyFile /etc/openvpn/ldap-client.key </LDAP> <Authorization> BaseDN "dc=rotreein,dc=my.id" SearchFilter "(uid=%u)" # (or choose your own LDAP filter for users) RequireGroup false </Authorization>
Create config file in /etc/stunnel/google-ldap.conf
[ldap] client = yes accept = 127.0.0.1:1636 connect = ldap.google.com:636 cert = /etc/openvpn/ldap-client.pem key = /etc/openvpn/ldap-client.key