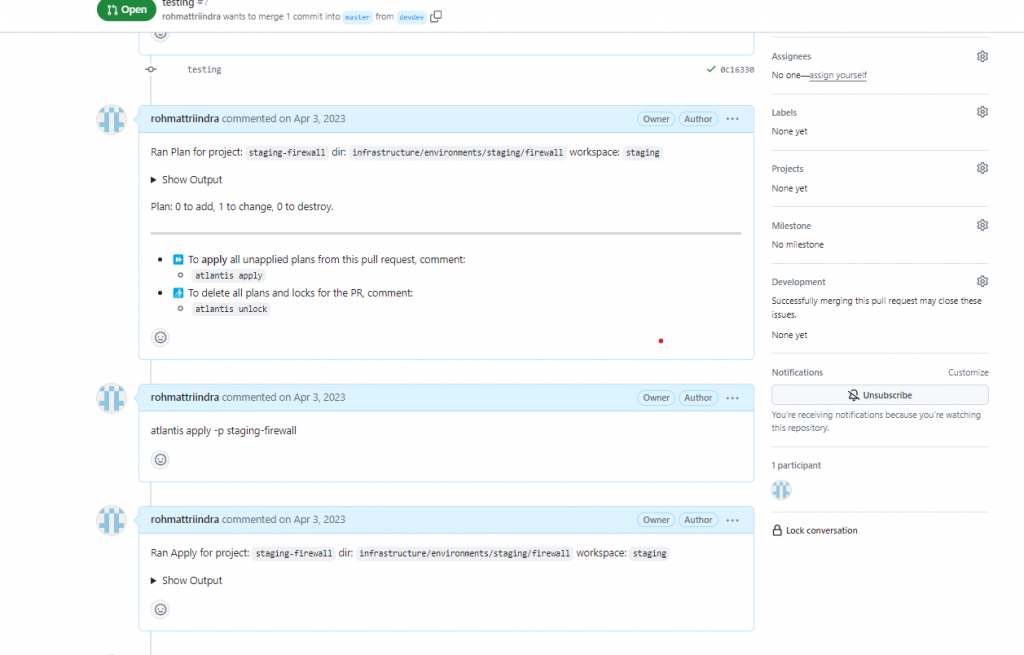
Atlantis is a powerful automation tool designed to streamline collaboration and code review workflows for Terraform infrastructure as code (IaC). It acts as a bridge between version control systems (VCS) like Git and Terraform, facilitating a smooth and efficient process for managing infrastructure changes
On this case, we deployed the Atlantis on Ubuntu VM
Install Terraform
wget https://releases.hashicorp.com/terraform/1.4.4/terraform_1.4.4_linux_amd64.zip unzip terraform_1.4.4_linux_amd64.zip sudo mv terraform /usr/local/bin/ terraform
Install Atlantis
sudo apt install git -y wget https://github.com/runatlantis/atlantis/releases/download/v0.23.3/atlantis_linux_amd64.zip unzip atlantis_linux_amd64.zip sudo cp atlantis /usr/local/bin/
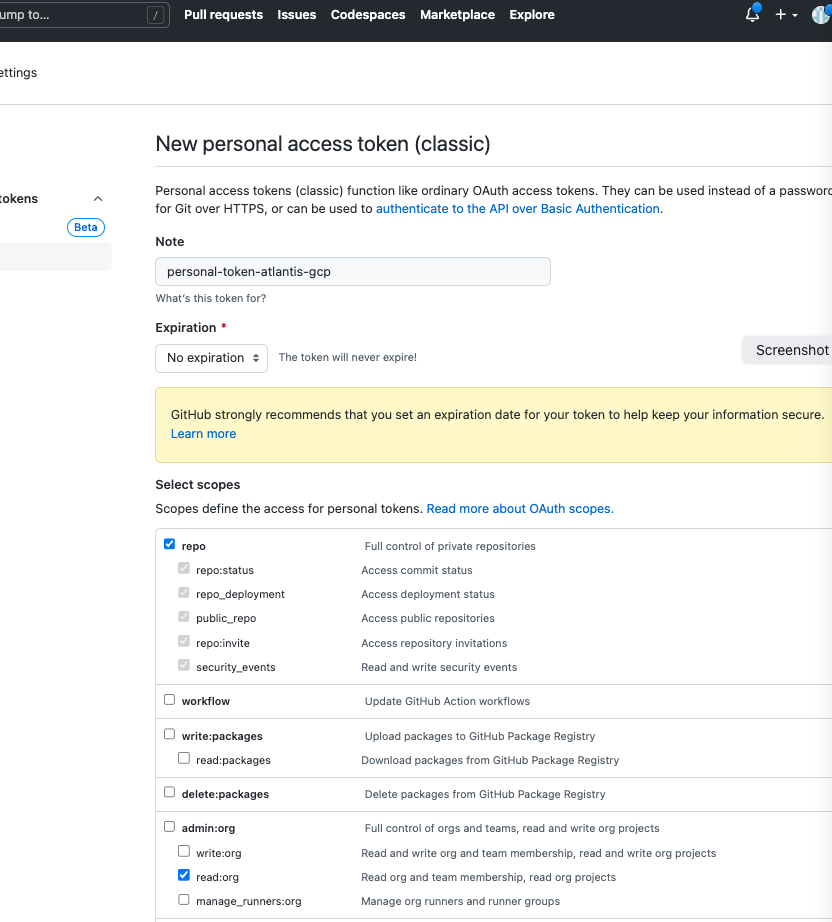
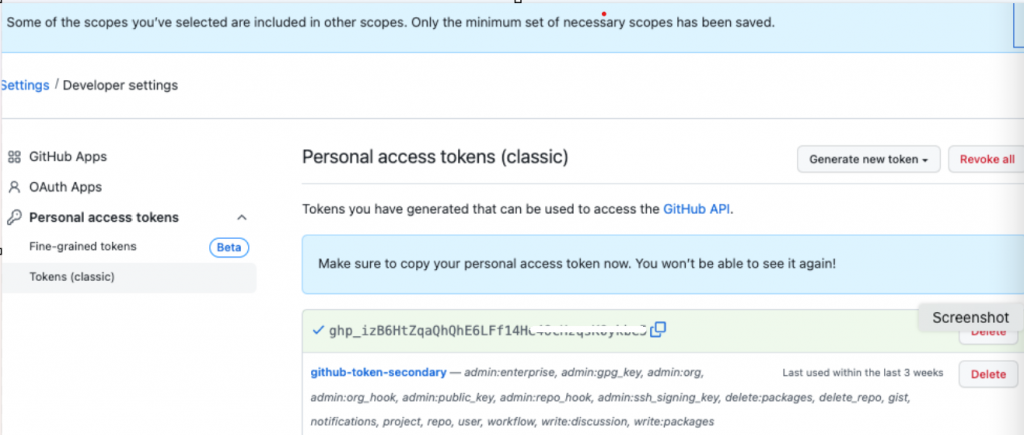
Create Personal Token
Create Service Account
Run the gcloud config command inside the Atlantis VM to set credential with service account
cloud_sandboxgcp_gmail_com@vm-atlantis-staging-1:~$ gcloud config set account 501066779977-compute@developer.gserviceaccount.com Updated property [core/account].
Create Altantis directory to store the Atlantis configurations
mkdir -p /opt/terraform/atlantis-workdi
Create repos.yaml on /opt/terraform/atlantis-workdir
repos: # Allow a specific repo to override. - id: github.com/rohmattriindra/tf-infra-gcp allowed_overrides: [apply_requirements, workflow] allow_custom_workflows: true apply_requirements: [approved]
Run the Atlantis server
atlantis server --atlantis-url=http://34.126.185.33 --gh-user=rohmattriindra --gh-token=ghp_VcOefm8MUwuoz3JU356yQtVDummy --gh-webhook-secret="0uNbW5pOBQfQvDummyDummyF" --repo-whitelist=github.com/rohmattriindra/tf-infra-gcp --data-dir=/opt/terraform/atlantis-workdir --repo-config=/opt/terraform/atlantis-workdir/repos.yaml
Create Atlantis.yml on the root directory, you can find sample on this repo https://github.com/rohmattriindra/tf-infra-gcp/blob/master/atlantis.yaml
version: 3
automerge: true
projects:
# staging-networks
- name: staging-network
dir: infrastructure/environments/staging/network
autoplan:
enabled: true
when_modified: ["../../../stack/network/*.tf*", "terraform.tfvars"]
workspace: staging
workflow: terraform
apply_requirements: [mergeable]. # without this command when we pu
workflows:
terraform:
plan:
steps:
- env:
name: PROJECT_DIR
command: echo $PROJECT_NAME | cut -d- -f2
- run: |
rm -rf .terraform
terraform -chdir="../../../stacks/$PROJECT_DIR/" init -backend-config=prefix="$WORKSPACE/$PROJECT_DIR" --reconfigure
terraform -chdir="../../../stacks/$PROJECT_DIR/" plan -var-file="../../environments/$WORKSPACE/$PROJECT_DIR/terraform.tfvars"
apply:
steps:
- env:
name: PROJECT_DIR
command: echo $PROJECT_NAME | cut -d- -f2
- run: |
terraform -chdir="../../../stacks/$PROJECT_DIR/" init -backend-config=prefix="$WORKSPACE/$PROJECT_DIR" --reconfigure
terraform -chdir="../../../stacks/$PROJECT_DIR/" apply --auto-approve -var-file="../../environments/$WORKSPACE/$PROJECT_DIR/terraform.tfvars"
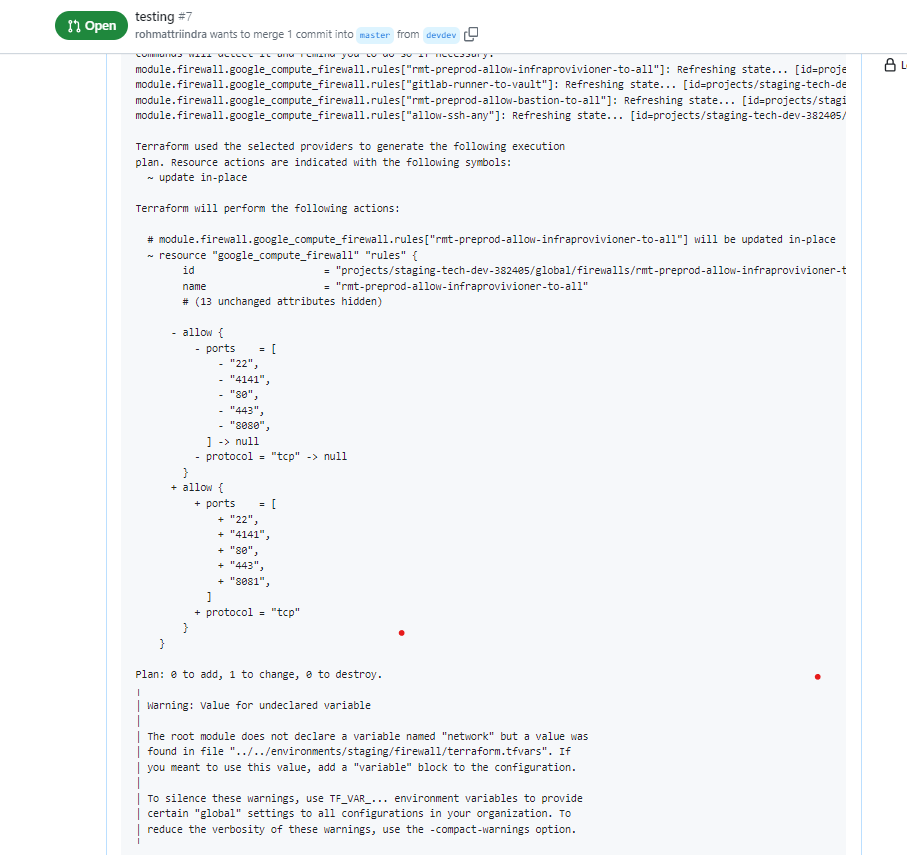
This is a sample result of the change in firewall resources